September 9, 2015 | Networks
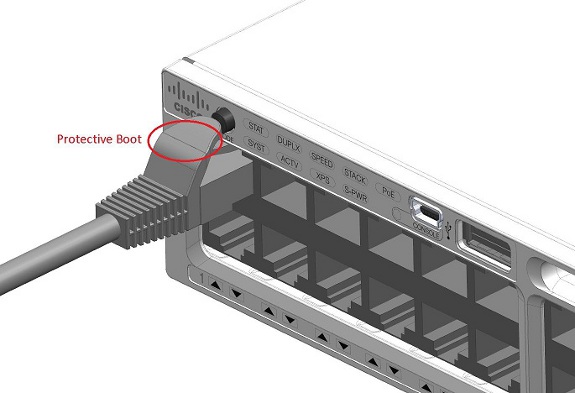
Way back in October 2013 Cisco slipped out this little field notice to customers and engineers across the globe. The position and function of the mode switch is such that it can be pressed by the protective boot on certain types of cables and cause a reset to factory settings. Problem Description Certain types of snagless […]
Read more
Tags: bug, cable, fail, reset
July 31, 2015 | Labs, Networks
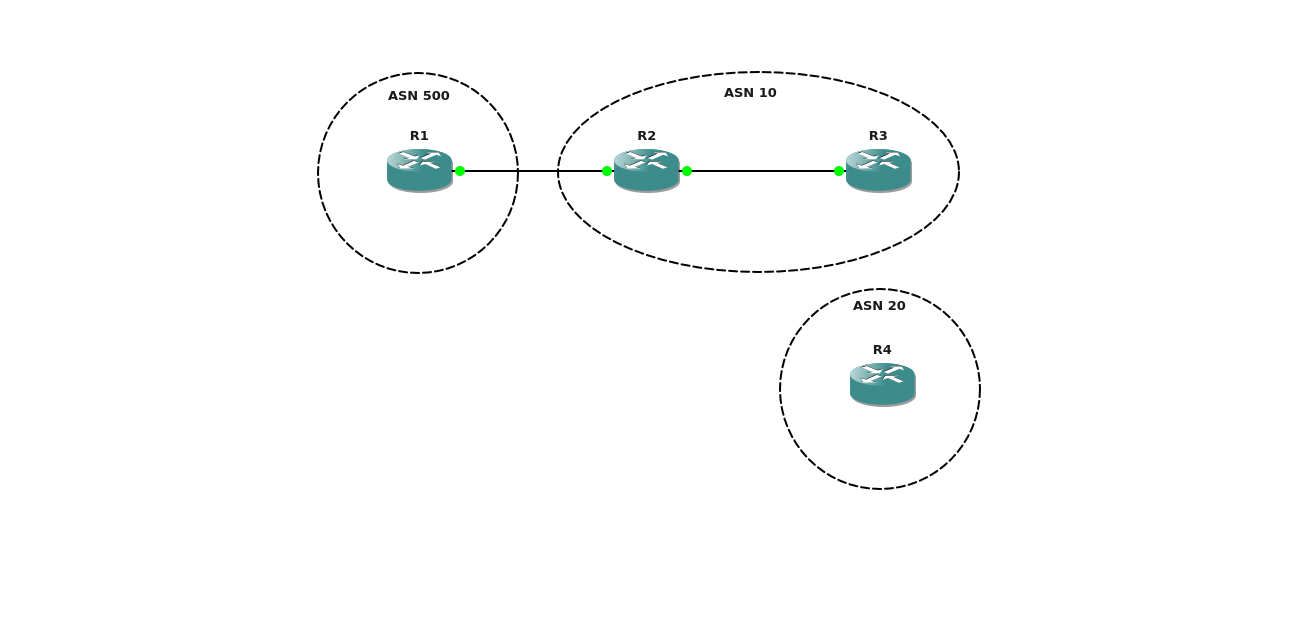
I am working on a project that involves moving a router from one BGP ASN to another. The topology above shows the current situation and we want to move R2 to ASN20 and have it hooked up to R4 instead of R3. Normally this would be pretty trivial however the owner of R1 in ASN […]
Read more
Tags: BGP, Routing, Routing Protocols
May 7, 2015 | Labs, Networks
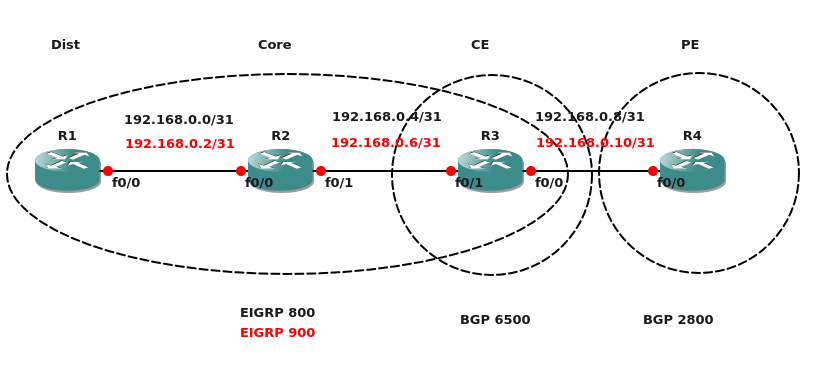
Some of my posts are just things that I was pretty sure worked but wasn’t 100% on how it worked and what the exact config looked like. In these situations if I can’t find something in a blog or on the Cisco site I post something to make it easier for the next guy trying […]
Read more
Tags: BGP, EIGRP, Routing, Routing Protocols
February 16, 2015 | Networks
I found a very clever site that does route summarisation from a list. This is ideal if you dump out a copy of your routing table and want to see where the routes can be summarised. It’s also useful if you have subnets for a firewall rule that you want to consolidate. http://www.netmatics.net/FreeTools/IPv4SupernetTools/SupernetCalc
Read more
Tags: Routing
February 4, 2015 | Labs, Networks, Security
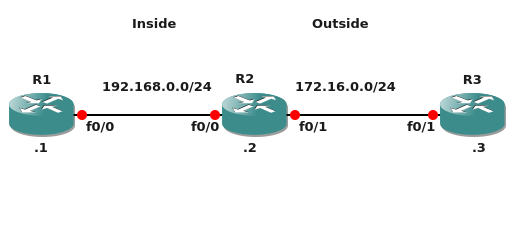
A colleague asked me to write a post on NAT and so this one is for him. I’m going to use a very basic three router lab to go through the common types of NAT and where they are used. First off there is the convention of inside and outside interfaces. The golden rule here is […]
Read more
December 10, 2014 | Networks, Security
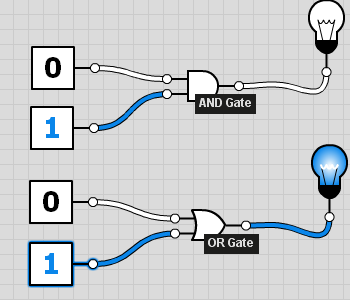
Having done an introduction to wildcard masks and the cool things you can do with them I thought it might be worth writing about the logic behind both subnet masks and wildcard masks. Masks use two of the most basic logical functions that computers can perform, a logical AND and a logical OR. Logical AND […]
Read more
December 9, 2014 | Networks, Security
If you ask most people what a wildcard mask is they’ll probably say it’s an inverse subnet mask. That is a massive under-representation of the power of a wildcard mask and does not do fair justice to the range of useful tricks you can do with a wildcard mask. We’ll start with why people think […]
Read more
September 24, 2014 | Networks, Security
In the past I always used ‘sh cry is sa’ to give me a view of the number of concurrent VPN sessions on an ASA. I am involved in an Anyconnect SSL VPN roll out and today I was asked to pull off stats on how many users are connected to each solution. The following […]
Read more
Tags: ASA, Security, VPN
September 16, 2014 | Networks
In this example I was playing around with OSPF areas. In the middle we have a backbone area with a standard area and three types of stub areas. R1 R2 R3 R4 R5 R6 R7 R8 R9 R10 In R1 we have all the routes we are expecting to see advertised from around the network. R1#sh ip route Codes: C – connected, S – […]
Read more
September 12, 2014 | Powershell, Scripting
I had a list of MAC addresses and was trying to identify them by finding out as much as I could about them. This was so I could document what devices I had found on which switchports in a datacenter. After looking them up in a router ARP table and doing a reverse DNS lookup […]
Read more